Single-Sign-On (SSO) Support
Impact+ supports a service provider (SP-initiated) SSO only. When SSO is configured, users initiate the login process by clicking a program link. This link routes the user to their company login for authentication, bypassing the Nitro registration and login. After authentication, users can directly access the Impact+ site.
Workflow
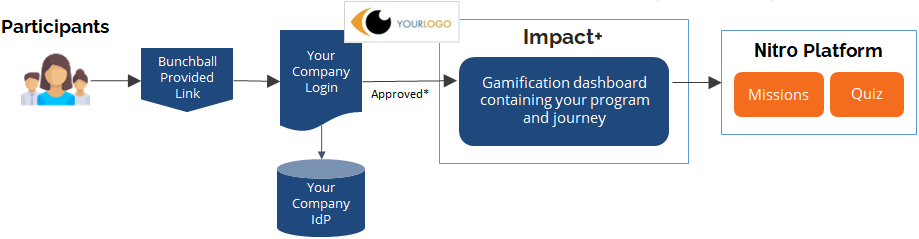
* The user’s Nitro UserID (gamification ID) and auth mapping must exist before the user can access the site.
General Checklist
Impact+ supports Single Sign-On (SSO) via SAML (Security Assertion Markup Language) and OIDC (OpenID Connect), providing secure and seamless authentication of users.
|
|
Task |
Details |
|---|---|---|
|
|
Provide the SSO login button name. |
The login button text can be customized when both SSO and self-registration are allowed. |
|
|
Determine if the SSO setup will also include self-registration. |
You can allow access via SSO only, or SSO plus self-registration. You must determine your access type before setup begins.
|
|
|
Provide a URL or test user for validation. |
Provide a method to test and validate login functionality. One or both of the following may be required:
|
|
|
Configure the user pool domain. |
Your system must allow authentication requests from Cognito by adding the user pool domain as an allowed callback. Note: Not all IdPs require setting up allowed callbacks. |
OIDC Checklist
The following are required to use OIDC authentication. Additional information may be requested as needed.
|
|
Task |
Details |
|---|---|---|
|
|
Provide a JSON file that maps OIDC attributes from your environment to Nitro. |
The file must contain the provider's configuration, including all necessary endpoints, tokens, and other metadata. Show me an example |
SAML Checklist
The following are required to use SAML authentication. Additional information may be requested as needed. After receiving this information, you will be given your SAML callback URL and SAML service provider identifier.
|
|
Task |
Details |
|---|---|---|
|
|
Ensure your Identity Provider (IdP) supports SAML 2.0. |
As a reliable party, Nitro is dependent on your access to an IdP that supports SAML 2.0. |
|
|
Provide a JSON file that maps SAML attributes from your environment. |
The file must indicate the SAML schemas that will map to gamification_id and preferred username. Additional mappings might include an email address. Show me an example A list of the common standard SAML identity claims is available at http://www.miicard.com/for/developers/ws-federation/supported-saml-claims |
|
|
Provide metadata documentation as an XML document or publicly available URL. |
If you have a customized logout URL, this should be included in the metadata file. Otherwise, the standard logout URL will be used.
|
See also

 This cannot be changed after creation.
This cannot be changed after creation.